
About
I’m currently Director Cyber Security Adversary Emulation heading the Red Team at Infineon Technologies. I have also been the founder and owner of x90.eu.
In the past, I was with secunet and worked with the Fraunhofer Institutes SIT and AISEC. This personal website expresses the opinions of none of those organizations.
As a member of several standardization committees and consortia I have been serving as a security expert to various technical standards and the European Commission.
I (co-)authored various publications and am a frequent public speaker at international automotive and security conferences and events.
I hold a Master’s degree in Practical Computer Science from FernUniversität in Hagen, Germany and a Bachelor’s degree in Computer and Media Security from the University of Applied Sciences in Hagenberg, Austria
I live with Martina, Darwin & Archimedes and spend my time in Munich / Germany, Wörthersee in the Austrian Alps and the Norwegian Fjords.
While on the road in between we reside in Franz-Ferdinand, our Campervan based on Mercedes Marco Polo.
Bio
Brief CV
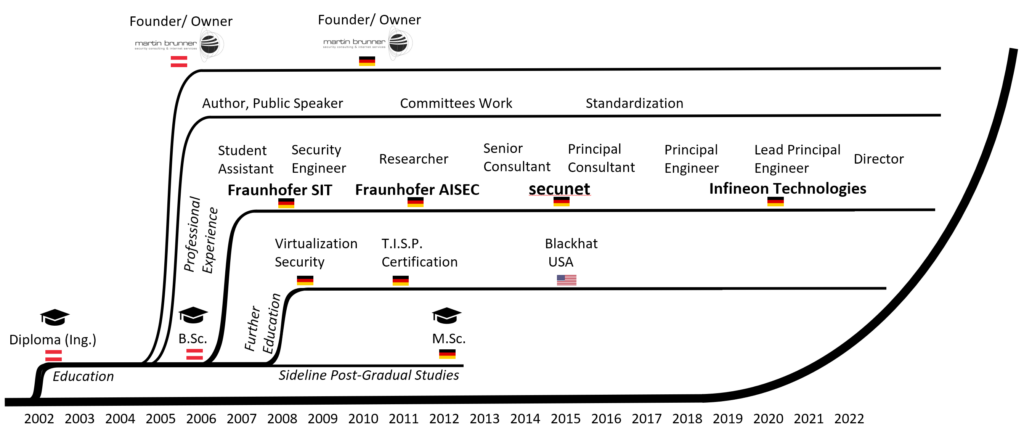

I founded my first company – a security-centric e-mail provider and hosting company – in 2005 during my first studies. Since 2006 I have been working as a security engineer, sysadmin, researcher, consultant, pen-tester, technical marketing manager and security architect for various industries and domains including but not limited to IT, Automotive, IoT, ICS, MNOs, Services Providers, Production, SME and Public Agencies.
Holding numerous research, engineering and consulting positions in automotive and security in an international environment and working with people from all over the world gave me the opportunity to learn about security from a variety of perspectives i.e., how security is perceived and handled by different positions, industries, applications, countries and cultures.
Overall, I have more than 15 years of global experience in IT- and automotive security – in designing, building, testing, operating and securing systems and networks.
Talks & Publications
I (co-)authored numerous papers, articles, patents and other sorts of publications and was honored to give talks on different occasions. Additionally, I contributed to various other technical documents, such as technical standards, whitepapers and guidelines.
A selection of these various activities is summarized below.
2022 |
Automotive Cyber Security at Infineon Talk Silicon Alps – Spotlight Cyber Security (Virtual), 2022. |
Security Threats, Regulations, Standards and Assurance Methods for Automotive Applications Whitepaper Global Semiconductor Alliance - Trusted IOT Ecosystem, 2022, (Whitepaper). |
2021 |
Towards standardized automotive security – must-haves for connected vehicles and V2X Talk Automotive Cybersecurity Webinar Series (Virtual), 2021. |
Trusted authentication of automotive microcontroller Patent US11177953B2, 2021. |
2020 |
Automotive Key Management – vom TPM zur vernetzten Lösung Talk Workshop IT Security on Board - Sicherheit in der Produktion, München, 2020. |
Safeguarding electric vehicle charging key to secure e-mobility Article In: FierceElectronics, 2020. |
Motor vehicle having a data network which is divided into multiple separate domains and method for operating the data network Patent EP3496975B1, 2020. |
2019 |
Trusted Platform Modules provide security for e-mobility Article In: eeNews Embedded, 2019. |
Future requirements for automotive hardware security Whitepaper Online, 2019, (Whitepaper). |
Sicherheit entscheidet sich im Gateway Article In: HANSER automotive, vol. 18, no. 10/2019, pp. 18–21, 2019. |
Hardware matters: how one chip can impact the security of a connected vehicle Conference PaperPeer-reviewed In: GmbH, VDI Wissensforum (Ed.): 19th International Congress ELIV 2019, pp. 455–468, VDI Verlag GmbH, Bonn, 2019. |
Post EVITA Semiconductor Security Quo Vadis? Conference PaperPeer-reviewed In: GmbH, VDI Wissensforum (Ed.): VDI-Fachtagung Automotive Security 2019 - Security, Datenschutz und die Neue Mobilität, pp. 51–70, VDI Verlag GmbH, Berlin, 2019. |
Paper Presentation: Hardware matters: how one chip can impact the security of a connected vehicle Talk 19th International Congress ELIV 2019, Bonn, 2019. |
Cover Story (Korean): TPM을 활용한 e-모빌리티 보안 향상 Article In: 전자기술 (Electronic Engineering), 2019. |
Introducing hardware-assisted security solutions based on HSM and TPM Talk Embedded Multi-Core Conference, Munich, 2019. |
Security als Teil der Architektur- Trusted Platform Module bietet Sicherheit für das Laden von EVs Article In: all-electronics, 2019. |
Trusted Platform Module - Sicherheit für das Laden von EVs Article In: emobility tec, vol. 02/2019, pp. 40–43, 2019, ISSN: 2193-892X. |
From hardware security towards trusted mobility: A semiconductor view on the security of connected vehicles Talk Vehicle Electronics & Connected Services 2019, Gothenburg, Sweden, 2019. |
Lightweight Authentication for Low-End Control Units with Hardware Based Individual Keys Conference PaperPeer-reviewed In: 2019 Third IEEE International Conference on Robotic Computing (IRC), pp. 425-426, IEEE, Naples, Italy, 2019. |
2018 |
Secure connectivity: Need for trust anchors in a connected car Talk Talk at Automotive Forum, electronica 2018, Munich, 2018. |
Easy to integrate semiconductor solutions for trusted mobility Talk Talk at Cyber Security Forum, electronica 2018, Munich, 2018. |
Paper Presentation: Leveraging Hardware Security to Secure Connected Vehicles Talk SAE WCX World Congress Experience, COBO CENTER - Detroit, MI, USA, 2018. |
Leveraging Hardware Security to Secure Connected Vehicles Conference PaperPeer-reviewed In: SAE WCX World Congress Experience, Technical Paper 2018-01-0012, SAE International SAE International in United States, 2018. |
Panelist Cyber Security Forum Panel electronica 2018, 2018. |
Kraftfahrzeug mit einem in mehrere getrennte Domänen eingeteilten Datennetzwerk sowie Verfahren zum Betreiben des Datennetzwerks Patent DE102017203185B4, 2018. |
2017 |
Trusted Platform Module - Automotive-Anwendungen und Abgrenzung zu HSM Talk 2. Vector Cyber Security Symposium, Stuttgart, Germany, 2017. |
2016 |
Automotive Ethernet – der nächste Schritt Talk Workshop IT Security on Board - New Technologies, München, 2016. |
Towards Secure Ethernet-based Vehicle Networks Talk Automotive Ethernet Congress 2016, Munich, 2016. |
IT-Sicherheit in Ethernet-basierten Fahrzeugnetzwerken: Offene Netze schützen Article In: Elektronik automotive, vol. 05.2016, 2016, ISSN: 1614-0125. |
2015 |
Neues aus dem Pentest-Lab Talk Workshop IT Security on Board - Hack me if you CAN, München, 2015. |
Kontrollierte Angriffe mittels Penetration Testing: Hack Me If You Can. Article In: Elektronik automotive, vol. 10.2015, pp. 44–48, 2015, ISSN: 1614-0125. |
Angriff auf die Autos von morgen Article In: secuview - The secunet Customer Magazine, 2015. |
2014 |
Industrie 4.0 - Security für Legacy Systeme Talk Workshop IT Security on Board - Sicherheitsbaukasten Automotive, München, 2014. |
2013 |
Angriffsvektoren und Schutzmaßnahmen am Beispiel App-gesteuerter Fahrzeugfunktionen Talk Workshop IT Security on Board - Fremd gesteuert und trotzdem sicher, München, 2013. |
Towards Next Generation Malware Collection and Analysis Journal ArticlePeer-reviewedArticle In: International Journal On Advances in Security, vol. 6, no. 1 & 2, pp. 32–48, 2013, ISSN: 1942-2636. |
Integrated honeypot based malware collection and analysis Book ChapterPeer-reviewed In: Zeilinger, Markus; Schoo, Peter; Hermann, Eckehard (Ed.): Advances in IT Early Warning, pp. 67–77, Fraunhofer Verlag Stuttgart, Stuttgart, 2013, ISBN: 9783839604748. |
2012 |
AWESOME - Automated Web Emulation for Secure Operation of a Malware-Analysis Environment Conference PaperPeer-reviewedBEST PAPER AWARD In: Proceedings of the Sixth International Conference on Emerging Security Information, Systems and Technologies (SECURWARE 2012), pp. 68-71, International Academy, Research, and Industry Association (IARIA) XPS, Rome, Italy, 2012, (BEST PAPER AWARD). |
Automated Web Emulation for Secure Operation of a Malware-Analysis Environment Talk PhD seminar at Institute for Security in Information Technology, TUM Department of Electrical and Computer Engineering - Technical University of Munich, 2012. |
Paper Presentation: AWESOME - Automated Web Emulation for Secure Operation of a Malware-Analysis Environment Talk Sixth International Conference on Emerging Security Information, Systems and Technologies (SECURWARE 2012),, Rome, Italy, 2012. |
Integrated Honeypot Based Malware Collection and Analysis Works for Qualification Fern Universität in Hagen, Faculty for Mathematics and Computer Science, 2012, (part-time via sideline additional postgraduate studies). |
2011 |
Integrated Honeypot Based Malware Collection and Analysis Talk Third International Workshop on Early Warning Systems in IT, Vienna, 2011. |
Problems in Web-Based OpenSource Information Processingfor IT Early Warning Conference PaperPeer-reviewed In: Web Intelligence for Information Security Workshop 2011, Lawrence Livermore National Lab.(LLNL) Lawrence Livermore National Lab.(LLNL), Lawrence Livermore National Lab.(LLNL), Livermore, CA (United States), 2011. |
Forschungsansätze zur Effizienzsteigerung heutiger IT-Frühwarnsysteme Journal ArticlePeer-reviewedArticle In: Datenschutz und Datensicherheit - DuD, vol. 35, iss. 4, pp. 253-257, 2011, ISSN: 1614-0702, (10.1007/s11623-011-0062-6). |
2010 |
Infiltrating critical infrastructures with next-generation attacks: W32.Stuxnet as a showcase threat Whitepaper 2010, ISSN: urn:nbn:de:0011-n-1513303. |
The Fraunhofer SIT MalwareAnalysis Laboratory - Establishing a Secured, Honeynet-based Cyber Threat Analysis and Research Environment Technical Report Fraunhofer-Institute for Secure Information Technology SIT Fraunhofer SIT Darmstadt, 2010. |
Anonymity and Privacy in Distributed Early Warning Systems Conference PaperPeer-reviewed In: 5th International Conference on Critical Information Infrastructures Security (CRITIS 2010), pp. 82–93, Springer, Athens, 2010, (ISBN 978-3-642-21693-0). |
MalCoBox: Designing a 10 Gb/s Malware Collection Honeypot Using Reconfigurable Technology Conference PaperPeer-reviewed In: Field Programmable Logic and Applications (FPL), 2010 International Conference on, pp. 592-595, IEEE Computer Society, Milan, Italy, 2010, ISSN: 1946-1488. |
Aktuelle F&E Arbeiten im Fraunhofer SIT Malware Lab Talk Linz, 2010. |
Packet Inspection Block Praktikum - Chair of IT Security - Department of Informatics - Technical University of Munich Lecture / Teaching 2010. |
2007 |
IT early warning systems – State-of-the-art and promising approaches to increase resilience of critical infrastructures Technical Report Fraunhofer-Institute for Secure Information Technology - SIT Department Secure Processes and Infrastructures - SPI, Schloss Birlinghoven, 53754 Sankt Augustin, Germany, 2007. |
2006 |
Hacking Talk Live Hacking Workshop, Informatik Tag Fraunhofer IZB, Fraunhofer-Institut für Sichere Informationstechnologie Schloss Birlinghoven 53754 Sankt Augustin, 2006. |
Remote DoS-Angriff auf den TCP/IP-Stack von OpenBSD Works for Qualification 2006, ((available in german only)). |
Konzeption und Aufbau eines Honeynet am Fraunhofer-Institut SIT Works for Qualification 2006. |
Das Server-Tagebuch Teil 3 - Nice To Have Article In: Hagenberger Kreis - Magazin zur Förderung der digitalen Sicherheit, 2006. |
2005 |
Das Server-Tagebuch Teil 1 - Must Have Article In: Hagenberger Kreis - Magazin zur Förderung der digitalen Sicherheit,, 2005. |
Das Server-Tagebuch Teil 2 - Services Article In: Hagenberger Kreis - Magazin zur Förderung der digitalen Sicherheit, 2005. |
Downloads
CV
Download my CV as PDF file
Press Kit
Download bio as PDF file
Contact
Get in touch
